You can let users login using external authentication authorities, through SSO.
This allows :
- to create Alpana Server accounts from external authorities, and from a single click
- to login to those Alpana Server accounts by relying on external authorities, and from a single click
To configure these external login configurations, go to the Host, in Settings and browse to the tab External Login Settings :
When configured, click Save all at the top right :
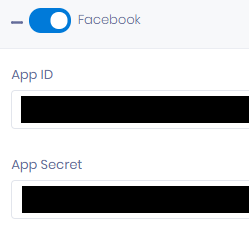
To use authentication through Facebook, fill-in the corresponding form :
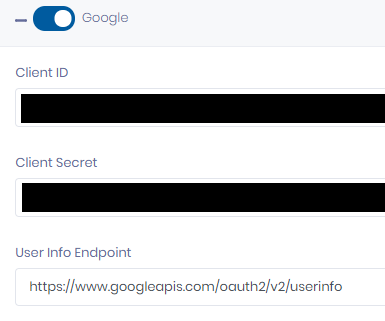
To use authentication through Google, fill-in the corresponding form :
Microsoft
(updated in 2020 R2)
Configuring on the Microsoft side
Create the app in Microsoft Developer Portal
Navigate to the Azure portal – App registrations page and create or sign into a Microsoft account:
If you don’t have a Microsoft account, select Create one. After signing in, you are redirected to the App registrations page:
- Select New registration
- Enter a Name.
- Select an option for Supported account types : “all accounts”, or equivalent (“All Microsoft account users”, etc)
- Under Redirect URI, enter the Alpana Server front-end URL including the port. An IP address is not supported, you must have a domain name (or optionally “localhost” for test purposes). For example :
http://mydomainname:123orhttp://localhost:4200 - Under “Implicit grant”, enable both Access tokens and ID tokens
- Select Register
Create client secret
- In the left pane, select Certificates & secrets.
- Under Client secrets, select New client secret
- Add a description for the client secret.
- Select the Add button.
- Under Client secrets, copy the value of the client secret, and store it.
Configuring on the Alpana side
In Alpana Server, use the client secret created above to fill in the values :
- Client Id : paste the Application (client) ID of your application from Microsoft
- Client Secret : paste the client secret copied above
WsFederation
(updated in 2020 R2)
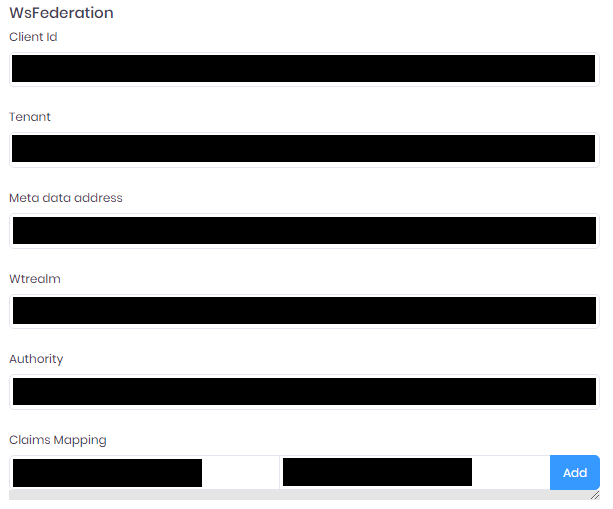
To use authentication through a WS-Federation authentication provider like Active Directory Federation Services (ADFS) or Azure Active Directory (AAD)., fill-in the corresponding form.
Below are some instructions to help with this.
Configuring on the Microsoft side
Follow the Microsoft documentation for ADFS and AAD.
As “Sign-on URL”, configure the Alpana Server Front-End URL.
Configuring on the Alpana side
In Alpana Server, use the values from the Active Directory client created above to fill in the values :
- Client Id : paste the Application (client) ID of your application from Microsoft. Example :
a1b2c3d4-xxxx-xxxx-xxxx-xxxxxxxxxxxx - Tenant : paste the Directory (tenant) ID of your application from Microsoft. Example :
a1b2c3d4-yyyy-yyyy-yyyy-yyyyyyyyyyyy - Meta data address : paste the Endpoints > Federation metadata document URL from Microsoft. Example :
https://login.microsoftonline.com/a1b2c3d4-yyyy-yyyy-yyyy-yyyyyyyyyyyy/federationmetadata/2007-06/federationmetadata.xml - Wtrealm : paste the Application ID URI from Microsoft. Example :
api://a1b2c3d4-xxxx-xxxx-xxxx-xxxxxxxxxxxx - Authority : paste the
https://sts.windows.net/<tenantid>/using the Tenant above. Example :https://sts.windows.net/a1b2c3d4-yyyy-yyyy-yyyy-yyyyyyyyyyyy/
OpenId Connect
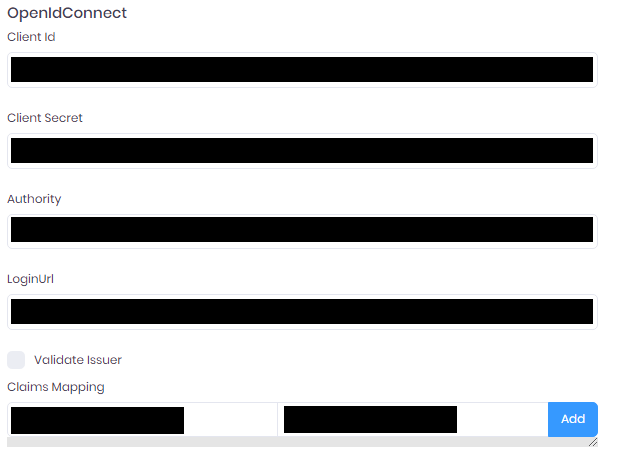
To use authentication through OpenId Connect, fill-in the corresponding form :
(new in 2020 R2)
To use authentication through Twitter, fill-in the corresponding form :




Post your comment on this topic.